How are your girls? Privacy leakage in information flows
One-way privacy settings are about as private as whispering to someone who insists on responding loudly (and often paraphrasing your whispers for good measure). So it is surprising that most, if not all, social networks allow one to specify the privacy of conversations flowing one way (those initiated by you) but not also of those flowing the other way (those initiated by others and directed at you).
Update: The New York Times has a piece that raises similar issues to my post. Here’s the relevant quote:
Yet an individual’s actions, researchers say, are rarely enough to protect privacy in the interconnected world of the Internet … You may not disclose personal information, but your online friends and colleagues may do it for you, referring to your school or employer, gender, location and interests … “Personal privacy is no longer an individual thing”
Polygamous Pimps
In response to a recent tweet in my buzz stream, a friend buzzed back:
“How are your girls?”
This particular buzz was public, which automatically meant all responses to it were public, including the utterly innocent question “How are your girls?”. Regardless of how air-tight my privacy settings in Google Buzz were, one can immediately infer some things about me: that I “have girls”. Most people would correctly understand that I am a father, though more creative readers may assume polygamy (or that I am a pimp).
Whatever your creative conclusions, one thing is for sure: an inadvertent leakage of my private details because of an inadequate online privacy model, one that largely regards privacy as flowing in one direction (uni-directional).
I am the captain of my ship. I am the master of my destiny.
Not when it comes to privacy, oh no!
Imagine a close friend bumped into you in a crowded elevator and asked how your new Viagra regimen is going on. From a privacy standpoint, you might as well have worn a Viagra costume to work, because the net effect is the same: an inadvertent leakage of your privacy. Assuming your friend had no ill intent, it is likely he was simply socially inept and did not realize the privacy implications of their question.
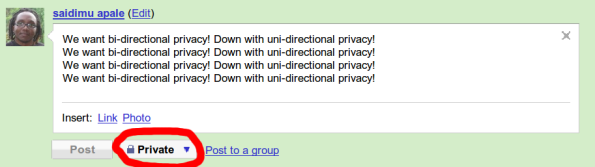
It is clear then, that we are neither captains of our privacy ship nor masters of our privacy destinies. Why then, do most social media sites continue this illusion? Some sites allow you to specify an outgoing post as being private (Google Buzz example below):
Two way street
As far as I can tell, no social site or app allows one to specify that conversations involving certain people will always be private, regardless of who initiated the conversation. This model of privacy correctly views information flow as a two way street (bi-directional), with privacy leakage capable of happening in either direction (you directly revealing your private information, or someone else revealing your private information while in conversation with you).
A number of chat applications implement such a privacy model in their “Off The Record” (OTR) features. Here is an excerpt from Google Talk’s description of their implementation:
We know that sometimes, we don’t want a particular chat, or chats with a specific person, to be saved … when chatting in Google Talk or Gmail, you can go “off the record,” so that nothing typed from that point forward gets automatically saved in anyone’s Gmail account.
… once you go off the record with a particular person, you will always be off the record with him or her, even if you close the chat window, and the two of you don’t chat again until several months later … We’ve designed this to be a socially-negotiated setting because we want to give users full disclosure and control over whether the person they’re talking to can save their chat. — What does it mean to go off the record
Wishful thinking
- I want to be able to go OTR with specific people, so that “nothing typed from that point forward gets automatically saved in anyone’s Gmail account.”
- I want this to be a “socially-negotiated setting” that does not make my privacy dependent on the technological awareness of my conversation partners.
- I want this setting to be persistent across all conversations involving specific people, whether one-or-one or in group conversations.Given the tight integration between Buzz and Gmail, it is not much of stretch to imagine a situation where a family member ask deeply personal questions in the midst of a public buzz stream involving my work.
In short, I want bi-directional privacy settings that work.
How about privacy leakage in conversations not involving me (from other people, to other people)?
Well, that’s a whole ‘nother can of worms.
M-PESA: the Black Swan of Mobile Money?
“A Black Swan … is an event with the following three attributes.
First, it is an outlier, as it lies outside the realm of regular expectations, because nothing in the past can convincingly point to its possibility.
Second, it carries an extreme impact.
Third, in spite of its outlier status, human nature makes us concoct explanations for its occurrence after the fact, making it explainable and predictable.”
— Nassim Nicholas Taleb, The Black Swan: The Impact of the Highly Improbable, in the New York Times
M-PESA: the Black Swan of Mobile Money?
Lately I have wondered whether the rise and stunning success of M-PESA is a Black Swan. M-PESA, a mobile money transfer service developed by/for Safaricom of Kenya, was launched in 2007 and has seen staggering growth. Much has been written about M-PESA and equivalent services worldwide (a search for M-PESA at CGAP yields a treasure-trove of articles). None of the launched services appear to rival M-PESA in growth, even in countries with similar target demographics (Tanzania, next-door to Kenya, isn’t doing so well with M-PESA).
Let Sleeping Dogs Lie
While there doubtless are many factors explaning the M-PESA phenomenon in Kenya, the implicit expectation always seems to be that it is just a matter of time before a similar service somewhere replicates M-PESA’s success in Kenya.
I’m not so sure anymore. Here’s why.
With M-PESA’s success in mind, and its implications for a country’s financial institutions, regulators (hardly known to be trend-setters) are unlikely to approve a service with as much leeway as Safaricom had with M-PESA.
Being the first to market what was essentially an outlier, Safaricom in effect escaped the regulators’ scrutiny in the early stages of M-PESA. Infact, once M-PESA’s success came to the attention of Kenya’s banking community and to the Central Bank, they tried regulating M-PESA in a way that would have, at the very least, hampered its growth. Here’s an illuminating quote from Kenya’s Daily Nation:
Bankers are up in arms over the revolutionary innovation. They have complained that cellphone companies are operating bank accounts outside of any regulations.
“Money transfer on the cellphone is a great idea,” John Wanyela, an executive director of the Kenya Bankers Association, told the Sunday Nation.
“But you do not allow innovation to outsmart regulation….[It] has broadened access to the unbanked, especially those in rural areas. We can’t do what they (mobile phone service providers) do. All we are asking for is a level playing ground.”
Banks have put the Central Bank of Kenya on the spot, demanding to know what laws allow telecommunication companies to offer money services, saying Zain and Safaricom are invading their domain without much regulation, while they continue to operate under the stringent rules of the Banking Act.
The appropriateness of the regulation isn’t my focus in this post, rather it is the effect of the regulation (appropriate or not) on the growth of M-PESA and similar services.
It is unlikely, so it appears at this moment, that regulators in other countries would give any company such leeway. It is also unlikely that financial institutions, with a lot to loose from an M-PESA clone, would sit tight and hope for the best. What is more likely is that constraints, whether the result of banking-industry lobbying or well-conceived government policy, will be placed on any such services.
MTN’s Mobile Money in Ghana
The latest launch of a mobile money service in Africa, in this case Ghana, bears out my theory (Appfrica has more details). The MTN service, which has seen slow uptake, seems hamstrung by rules and regulations forced on it by banks and regulators in Ghana.
From the Appfrica article, MTN’s Mobile Money seems to burden merchants and customers in ways that Safaricom’s M-PESA does not. With MTN’s system:
- customers need ID to perform *any* transaction
- merchants are required to have a specific handset for customer registration (something Kenya’s Zain (then known as Celtel) tried and failed with Sokotele, its earlier attempt at mobile money (Zap is Zain’s current money transfer service).
- customers have to sign for every transaction
- merchants need a bank account from participating banks
- the growth of the money-transfer network depends on banks expanding and accepting more merchants
Part of the reason for M-PESA’s runaway success has been its relative simplicity and lack of constraints, from the merchant/customer perspective. Fraud levels are somehow, and curiously, kept to a “manageable” level (if the lack of public outcry from Kenyans is anything to go by).
White Swans Galore
Sadly, it appears that M-PESA was an anomaly that won’t be replicated elsewhere anytime soon.
M-PESA succeeded, it appears, largely because there was no precedent, and hence little legislation standing in the way.
Perhaps regulators ought to factor this into their deliberations.
The Professionalization of the Consumer
Cry Me A River
Here’s an interesting quote from a post at Engadget.com discussing the Microsoft/Sidekick/T-Mobile cloud fiasco. I’m trying hard to resist saying it was quite a storm.
What’s happening now is the IT-ization of the consumer. It’s a world where the head of house is CIO, the spouse runs the help desk and the kids do tech support. (Johnny, stop practicing piano and please get those Windows 7 security updated installed.) Of course, the consumer does it with no budget, resources, trained professionals or skills. This is a huge problem and the data issues we saw with Sidekick are just the tip of the iceberg.
Hmm… I’m tempted to say this is unique to the technologies of our age, that we are witnessing a truly unfortunate democratization of specialization (yeah, I know it’s a mouthful but bear with me). Except that it isn’t unique to our age or to our technologies and isn’t altogether unfortunate.
History Has A Nasty Habit Of Repeating Itself
Every generation, when faced with vexing problems, almost always laments the uniqueness of its challenges. I’m not entirely certain why this is so but I suspect it may offer some consolation for one’s inability to cope. As far as therapies go this may be a good one. Here are some counter-examples of the uniqueness theorem:
- Healthcare: the medicalization of living, coupled with ready access to health information, has forced many to be virtual healthcare experts. How often do we Google different diagnoses and therapies?
- Investments: shopping for a investment adviser is itself an exercise in mini-specialization. The depth of knowledge required is simply beyond what can safely be categorized as general knowledge. It is specialty knowledge.
As technology, for better or for worse, increases its hold on our lives, greater depth of knowledge will be expected of the general populace (what I call the democratization of specialization). I’m willing to bet on for better, despite the very real problems this view presents. Today’s specialty is tomorrow’s commodity, so dictates the marketplace of ideas.
Why This Is A Good Thing
Just as commoditization of goods and services leads to value creation higher up the chain, so does this transformation of yesterday’s specialty knowledge into today’s general knowledge.
I’m not a social scientist so I cannot back this up, but my feeling is that a better-informed population tends to make better choices, overall, for society.
And that is what progress is all about, right?
Update (Nov. 1, 2009):
Here is an interesting video on participatory medicine, a.k.a Health 2.0:
Participatory medicine is a product of its time: advances in medical technologies place increasing responsibility on individuals for their health care, while advances in different technologies make it increasingly possible for them to assume those responsibilities without attending medical or nursing school. Both kinds of technologies are tools designed to contribute to better outcomes. But the technologies do not constitute participatory medicine. Rather they enable it. Without tools ? insulin pumps, comparative quality ratings, in-home dialysis, and online patient groups, for example — participatory medicine would simply not be possible.
An excerpt from an article on the technical underpinnings of participatory medicine in the Journal of Participatory Medicine, a great journal even for healthcare laypersons (like me).
.